The End of Passwords? Apple, Google, and Microsoft Team Up to Revolutionize Online Authentication

Introduction:
Passwords have long been the primary means of securing online accounts, but they are not without their flaws. Weak passwords, password reuse, and phishing attacks are just a few examples of the problems that can arise when relying on passwords. Apple, Google, and Microsoft, three of the biggest names in technology, are collaborating to support a new password-free login method as a solution to these problems.
The Problem with Passwords:
Passwords are a ubiquitous feature of the modern online landscape. From banking to social media, nearly every website and app requires a password to log in. However, passwords have many problems. For starters, people often choose weak or easily guessable passwords, making them vulnerable to brute-force attacks.
Additionally, people often reuse passwords across multiple accounts, which can lead to devastating consequences if one of those passwords is compromised. Lastly, phishing attacks are a growing concern, as hackers attempt to trick users into divulging their passwords through fraudulent emails and websites.
The Solution:
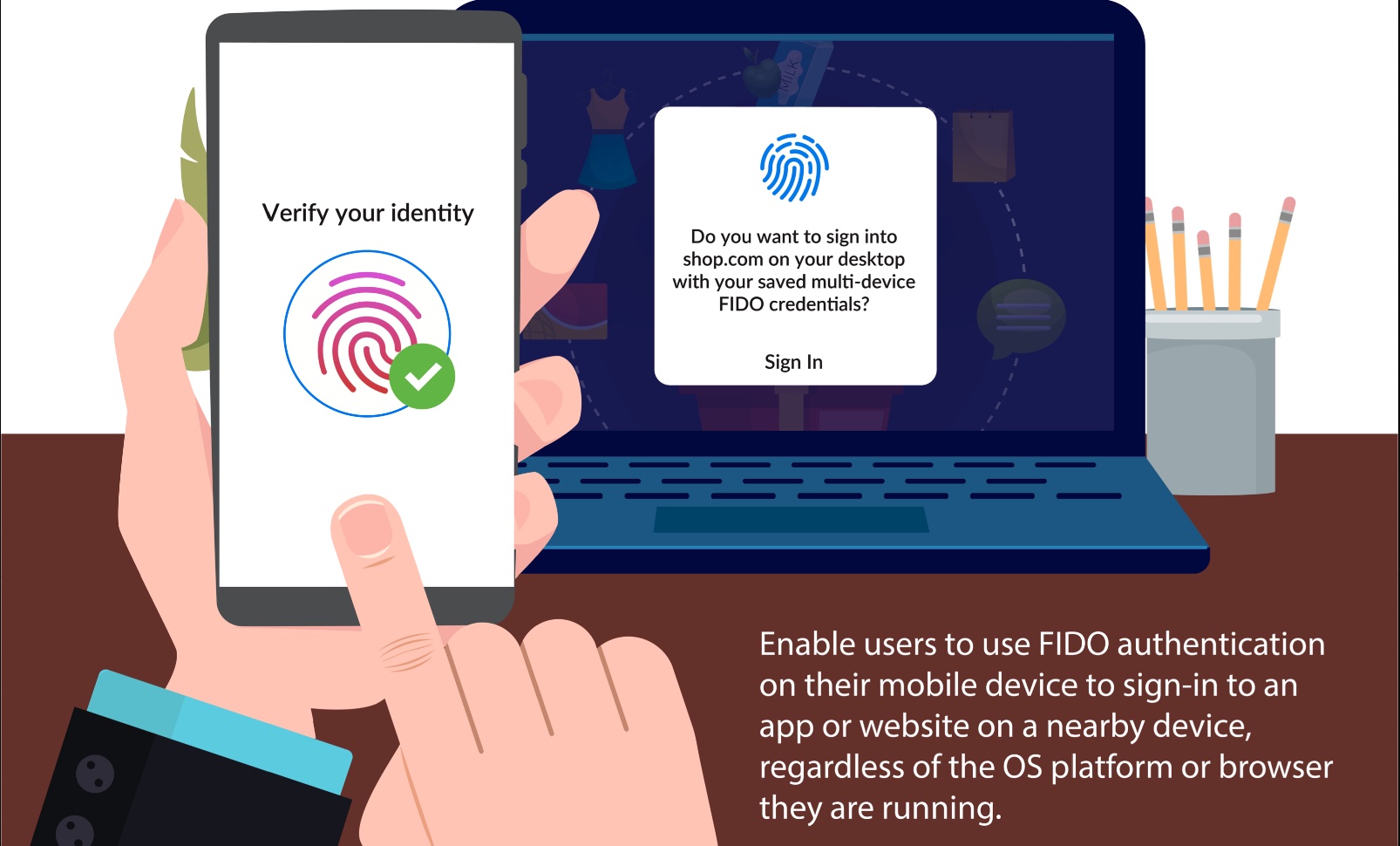
Apple, Google, and Microsoft are collaborating to support a new password-free login method as a solution to these problems. The solution is based on an open standard called WebAuthn, which allows users to log in using biometric data, such as fingerprints or facial recognition, or physical security keys. By using biometric data or physical security keys, users can eliminate the need for passwords altogether. This approach provides several benefits, including improved security, ease of use, and reduced reliance on passwords.
Improved Security:
By eliminating the need for passwords, this new approach greatly improves security. Passwords are notoriously weak, and even complex passwords can be easily cracked with the right tools. Biometric data and physical security keys, on the other hand, are much harder to fake or steal. This means that users can enjoy greater peace of mind knowing that their accounts are more secure.
Ease of Use:
One of the biggest benefits of this new approach is its ease of use. Logging in with biometric data or physical security keys is much faster and more convenient than typing in a password. Users can simply tap their fingerprints or insert their security key to log in, without having to remember a password or worry about typos.
Reduced Reliance on Passwords:
Lastly, this new approach reduces our reliance on passwords. By eliminating passwords, we can greatly reduce the risk of password-related problems such as weak passwords, password reuse, and phishing attacks. Additionally, this approach allows users to use the same authentication method across multiple websites and apps, reducing the need to remember multiple passwords.
The downside of ending passwords:
While the idea of ending passwords may seem appealing, there are potential downsides and concerns to consider. One of the main concerns is security risks. Replacing passwords with other forms of authentication such as biometrics or one-time codes can potentially create new security risks.
Another concern is dependent on technology, as the new authentication methods may rely on technology that not everyone has access to or may experience technical difficulties with. Centralization is also a potential issue, as a few major companies controlling the new authentication systems could create a centralized point of control, raising data privacy concerns or even abuse of power.
User privacy is another issue, as the use of biometrics or other forms of authentication may require the collection and storage of sensitive personal data, raising questions about privacy and data protection. Finally, accessibility is also a concern, as passwords are still widely used because they are accessible to most people regardless of their physical or cognitive abilities. Any new authentication systems should be carefully designed and implemented to take these potential drawbacks into account.
Conclusion:
In conclusion, the tech giants Apple, Google, and Microsoft are working together to support a new way for people to log in to accounts without using passwords. This approach is based on an open standard called WebAuthn, which allows users to log in using biometric data or physical security keys.
This new approach provides several benefits, including improved security, ease of use, and reduced reliance on passwords. By eliminating passwords, we can greatly reduce the risk of password-related problems and provide users with a more secure and convenient way to log in.







